Now of course we are all aware of what comes to mind when you say "Brute Force" but what about another use? What if crappy entropy produces a value that is say AJJDAJJDASDFHGHABC but only the last three characters "ABC" change? This could be a session value and could be attacked as discussed in Sequencer & Entropy OR it could be value such as 'resource=' which renders sensitive content. Your profile and the resource it can access might be client-side controllable and it may be as simple as iterating thru all possible combinations of that value.
In our scenario we will say that our sequencer has informed us of the weak entropy and those last three characters iterate between different combinations of ABCDEF (but not the rest of the alphabet) and only use upper case characters.
By now I assume you know how to load a payload or 'request' into Intruder. If not, reference any of the other BToDs for clarification. Navigate to Burp > Intruder > Positions Tab. Add position points around 'ABC' since this is what we will be iterating thru and collecting the responses.
Should look like this:
Next, navigate to Intruder > Payloads. Drop down the payload set list and choose 'brute forcer'.
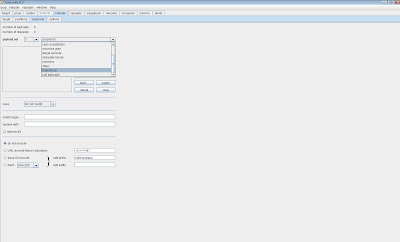
In the picture below I show what the default settings are and the 4 settings we care about. Remember we know we will only use the characters ABCDEF, they will only be three characters and finally they will always be uppercase.
Character set - only include the characters we are interested in, the min and max length is 3 and case is Uppercase. Should look like this:
We are all set. Now start attacking............
Use the results to check for byte length (if attacking a session) or save the responses to prove to your customer you can view data that you should not be able to. Either way, enjoy.
Happy Hacking!





No comments:
Post a Comment