Customers understand better when you actually show them the data that you can extract. Time and again I've observed a simple numerical value used as your USER ID and time and again its client side controllable. The easiest way to automate this attack and extract useful data, for me at least, has been to use the Burp Suite > Intruder 'number' payload along with the Intruder > 'grep' function all contained within the suite.
Lets go!
Step number one is to request the URI that points to your profile and intercept that request.
Now that the payload has been sent to intruder lets go over to the Intruder > positions tab. Clear the the current positions by selecting 'clear' button on the right. Then add the positions by selecting 'add' on either side of the numerical value. Ensure the attack type selected is 'Sniper.
After this has been accomplished move over to the Intruder > payloads tab. Scroll down at payload set to 'numbers'.
We are now ready to configure the numbers payload. We've selected from 0 to 1000 (Numerical representation of USER IDs). We've done this by adding 0 in the Intruder > payloads > range 'from' field and 1000 in the 'to' field. Since 1000 is four digits I've entered the number 4 in the 'Max Integer Digits' field. The 'Min Integer Digits' field is set at 1 since we need at least 1 integer. The 'step' field is set at 1 because I only want to increment 1 digit at a time. For example, 1 2 3 4, etc etc. Lastly, the 'sequential' radio button has been highlighted as well as the 'decimal' radio button for obvious reasons. These are decimal values incrementing sequentially.
Now lets say we want to grep a field named "dob" for the results. This represents a field named "dob" which contains customers dates of birth. We will later use this output to fill an excel sheet or whatever you prefer Navigate to Intruder > options and scroll down the page to 'grep'. Click the extract tab. So to extract the string in the response I added dob= (this is how it would look in the raw response) and chose to stop capturing at "> (this is where the field ends). I also chose 'simple pattern match' for simplicity's sake. NOTE: If the response containing this field comes only after a 302 response or "redirection" choose to follow redirects. If you follow redirects you probably want to process cookies. All depends on the behavior of the application.
So now that this is configured, its time to fire up intruder. Go to the very top of burp, drop down intruder and click 'start'. At this point you should see your intruder fill up with responses containing the dob value. Note: I'm not doing this on a real site, therfore you will see no results in my dob field. You get the point.
At this point you can save your results by choosing save > attack results but I believe this functionality is limited to users of the professional version found Here . I'm sure you can figure something out in the interim!
Monday, August 31, 2009
Sunday, August 30, 2009
Using Burp Intruder to brute force login
Inspired by a little tweet I saw from @carnal0wnage, I've decided to make today's "Burp Tip of the Day" about brute forcing a login with Burp Suite's Intruder. As always, this goes a lot faster if you purchase the professional version of Burp here. However, this also works for the free version but much slower.
So, lets get started!
First thing first, send a request to the target site entering a username and password combo. I chose pma_username=test and pma_password=test. Intercept that request, right click and send to intruder like so.
Once you have the request sent to burp 'Intruder' you need to choose your targets for the intruder payload. You can do this by clicking the 'add' button and putting the '$' symbol around the username and password as shown in the example. Also choose the 'cluster bomb' attack type (circled in the example).
Next step is to roll over to the Intruder > Payloads tab. You will have two separate payload sets. Set 1 and Set 2 (easy right?). So in payload Set 1 you choose "preset list" click 'load' and upload the user_name file (containing....ya you guessed it). It should look like so:
Next, click payload set 1 and drop down to payload set 2. You remain using a preset list and click 'load' to upload the password file. It should look like so:
At this point you are ready to rock. Just in case the password submission is using Basic Authorization (aka Base64) you can choose to base64 encode the data by choosing the option in the Intruder > payload section near the bottom. So go to the very top, drop down intruder, and click start. All in all the results should look something like this:
Generally when the length differs greatly or the response code differs you have a pretty good sign that you've hit the mark! Hope this helps someone.
So, lets get started!
First thing first, send a request to the target site entering a username and password combo. I chose pma_username=test and pma_password=test. Intercept that request, right click and send to intruder like so.
Once you have the request sent to burp 'Intruder' you need to choose your targets for the intruder payload. You can do this by clicking the 'add' button and putting the '$' symbol around the username and password as shown in the example. Also choose the 'cluster bomb' attack type (circled in the example).
Next step is to roll over to the Intruder > Payloads tab. You will have two separate payload sets. Set 1 and Set 2 (easy right?). So in payload Set 1 you choose "preset list" click 'load' and upload the user_name file (containing....ya you guessed it). It should look like so:
Next, click payload set 1 and drop down to payload set 2. You remain using a preset list and click 'load' to upload the password file. It should look like so:
At this point you are ready to rock. Just in case the password submission is using Basic Authorization (aka Base64) you can choose to base64 encode the data by choosing the option in the Intruder > payload section near the bottom. So go to the very top, drop down intruder, and click start. All in all the results should look something like this:
Generally when the length differs greatly or the response code differs you have a pretty good sign that you've hit the mark! Hope this helps someone.
Saturday, August 29, 2009
BurpSuite Intruder Tip (Creating a site map quickly!)
Until I have another program (qwick_request.rb) correctly coded to properly handle certain errors when requesting the output of DirSnatch (which is just a bunch of URIs) thru the proxy............I've been using BurpSuite v1.2 Intruder functionality instead to build an application map.
Note: If you are using the professional version of BurpSuite you can build an entire site map very very quickly even if it has thousands of resources and 404 errors, 500, etc etc (due to unauthed permissions). Visually it can be easier and also you may have unexpected results when requesting a resource you shouldn't have permissions to. This is why I do this.
Overview:
Basically I use the output of DirSnatch (minus the URL) as a payload for BurpSuite Intruder. I start intruder running that payload and because it is forwarding to the second instance of Burp, you will see the target tab fill up very quickly if you are using the professional version. Slower for the free version (not threaded).
So, I've already spidered a site and created a payload file (as an example). Here is what a payload for something like sourceforge.net would look like.
Then I send a request for simply http://sourceforge.net and intercept that request with burp. When the request is intercepted (in the proxy tab) Right click and choose "Send to Intruder".
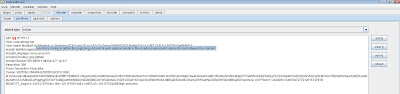
We are almost good to go! So scroll over to the comms tab (newer version called options). Scroll down to 'use proxy server'. Enter the IP address (127.0.0.1) and enter the port number (i'm using 8081, cant have two instances of Burp on the SAME machine and BOTH running on port 8080 due to .......ummm....science?) and then DO NOT 'CLICK USE PROXY SERVER' yet anyways :).
Fire up that second BurpSuite instance. Under the Proxy tab > options you will see "Proxy Listeners". Highlight the entry that shows port 8080 and click 'edit'. When the local listener port is populated with 8080 change to 8081. (If you want to run the second burpsuite instance on another machine - uncheck 'listen on loopback interface only' and CHECK 'support invisible proxying for non-proxy-aware-clients') and then..........update. Also, make sure the 'running' column is checked. NOW you can go back to the first instance of BurpSuite and click 'use proxy server'. Should look like this:
Finally, we are ready to start. Back at your first instance of BurpSuite, at the VERY TOP of the BurpSuite program you will see 'Intruder' (not the tab, look even farther up). So, now that you are at the intruder drop down, click start. If you go back to your second burpsuite instance you will notice the target tab has filled up. Great success!
Note: If you are using the professional version of BurpSuite you can build an entire site map very very quickly even if it has thousands of resources and 404 errors, 500, etc etc (due to unauthed permissions). Visually it can be easier and also you may have unexpected results when requesting a resource you shouldn't have permissions to. This is why I do this.
Overview:
Basically I use the output of DirSnatch (minus the URL) as a payload for BurpSuite Intruder. I start intruder running that payload and because it is forwarding to the second instance of Burp, you will see the target tab fill up very quickly if you are using the professional version. Slower for the free version (not threaded).
So, I've already spidered a site and created a payload file (as an example). Here is what a payload for something like sourceforge.net would look like.
Then I send a request for simply http://sourceforge.net and intercept that request with burp. When the request is intercepted (in the proxy tab) Right click and choose "Send to Intruder".
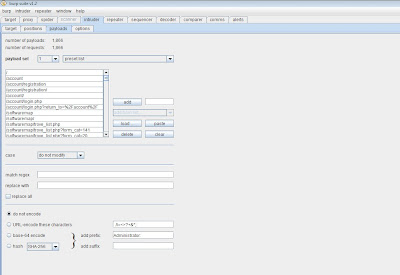
Once the request is in the "Intruder tab", go to the Intruder tab (duh) and clear the payload selector. Add the variable you want to "fuzz" by clicking 'add' on either side of the "forward slash" on the first line. You can leave the "Sniper" attack type in place.

At this point you want to move out of the Intruder > positions tab over to Intruder > payloads tab. Under payload set you will see "load". Once you click load you can load the payload file. It should look like this when you are done. (Notice: choose 'Do not URL encode these characters'). This is important., by default it is enabled and this will cause issues with what we are doing.

We are almost good to go! So scroll over to the comms tab (newer version called options). Scroll down to 'use proxy server'. Enter the IP address (127.0.0.1) and enter the port number (i'm using 8081, cant have two instances of Burp on the SAME machine and BOTH running on port 8080 due to .......ummm....science?) and then DO NOT 'CLICK USE PROXY SERVER' yet anyways :).
Fire up that second BurpSuite instance. Under the Proxy tab > options you will see "Proxy Listeners". Highlight the entry that shows port 8080 and click 'edit'. When the local listener port is populated with 8080 change to 8081. (If you want to run the second burpsuite instance on another machine - uncheck 'listen on loopback interface only' and CHECK 'support invisible proxying for non-proxy-aware-clients') and then..........update. Also, make sure the 'running' column is checked. NOW you can go back to the first instance of BurpSuite and click 'use proxy server'. Should look like this:
Finally, we are ready to start. Back at your first instance of BurpSuite, at the VERY TOP of the BurpSuite program you will see 'Intruder' (not the tab, look even farther up). So, now that you are at the intruder drop down, click start. If you go back to your second burpsuite instance you will notice the target tab has filled up. Great success!

















