Customers understand better when you actually show them the data that you can extract. Time and again I've observed a simple numerical value used as your USER ID and time and again its client side controllable. The easiest way to automate this attack and extract useful data, for me at least, has been to use the Burp Suite > Intruder 'number' payload along with the Intruder > 'grep' function all contained within the suite.
Lets go!
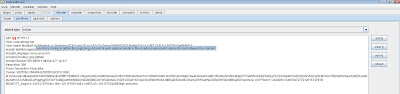
Step number one is to request the URI that points to your profile and intercept that request.
Now that the payload has been sent to intruder lets go over to the Intruder > positions tab. Clear the the current positions by selecting 'clear' button on the right. Then add the positions by selecting 'add' on either side of the numerical value. Ensure the attack type selected is 'Sniper.
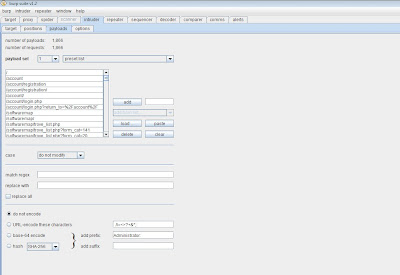
After this has been accomplished move over to the Intruder > payloads tab. Scroll down at payload set to 'numbers'.
We are now ready to configure the numbers payload. We've selected from 0 to 1000 (Numerical representation of USER IDs). We've done this by adding 0 in the Intruder > payloads > range 'from' field and 1000 in the 'to' field. Since 1000 is four digits I've entered the number 4 in the 'Max Integer Digits' field. The 'Min Integer Digits' field is set at 1 since we need at least 1 integer. The 'step' field is set at 1 because I only want to increment 1 digit at a time. For example, 1 2 3 4, etc etc. Lastly, the 'sequential' radio button has been highlighted as well as the 'decimal' radio button for obvious reasons. These are decimal values incrementing sequentially.
Now lets say we want to grep a field named "dob" for the results. This represents a field named "dob" which contains customers dates of birth. We will later use this output to fill an excel sheet or whatever you prefer Navigate to Intruder > options and scroll down the page to 'grep'. Click the extract tab. So to extract the string in the response I added dob= (this is how it would look in the raw response) and chose to stop capturing at "> (this is where the field ends). I also chose 'simple pattern match' for simplicity's sake. NOTE: If the response containing this field comes only after a 302 response or "redirection" choose to follow redirects. If you follow redirects you probably want to process cookies. All depends on the behavior of the application.
So now that this is configured, its time to fire up intruder. Go to the very top of burp, drop down intruder and click 'start'. At this point you should see your intruder fill up with responses containing the dob value. Note: I'm not doing this on a real site, therfore you will see no results in my dob field. You get the point.
At this point you can save your results by choosing save > attack results but I believe this functionality is limited to users of the professional version found Here . I'm sure you can figure something out in the interim!
Lets go!
Step number one is to request the URI that points to your profile and intercept that request.
Now that the payload has been sent to intruder lets go over to the Intruder > positions tab. Clear the the current positions by selecting 'clear' button on the right. Then add the positions by selecting 'add' on either side of the numerical value. Ensure the attack type selected is 'Sniper.
After this has been accomplished move over to the Intruder > payloads tab. Scroll down at payload set to 'numbers'.
We are now ready to configure the numbers payload. We've selected from 0 to 1000 (Numerical representation of USER IDs). We've done this by adding 0 in the Intruder > payloads > range 'from' field and 1000 in the 'to' field. Since 1000 is four digits I've entered the number 4 in the 'Max Integer Digits' field. The 'Min Integer Digits' field is set at 1 since we need at least 1 integer. The 'step' field is set at 1 because I only want to increment 1 digit at a time. For example, 1 2 3 4, etc etc. Lastly, the 'sequential' radio button has been highlighted as well as the 'decimal' radio button for obvious reasons. These are decimal values incrementing sequentially.
Now lets say we want to grep a field named "dob" for the results. This represents a field named "dob" which contains customers dates of birth. We will later use this output to fill an excel sheet or whatever you prefer Navigate to Intruder > options and scroll down the page to 'grep'. Click the extract tab. So to extract the string in the response I added dob= (this is how it would look in the raw response) and chose to stop capturing at "> (this is where the field ends). I also chose 'simple pattern match' for simplicity's sake. NOTE: If the response containing this field comes only after a 302 response or "redirection" choose to follow redirects. If you follow redirects you probably want to process cookies. All depends on the behavior of the application.
So now that this is configured, its time to fire up intruder. Go to the very top of burp, drop down intruder and click 'start'. At this point you should see your intruder fill up with responses containing the dob value. Note: I'm not doing this on a real site, therfore you will see no results in my dob field. You get the point.
At this point you can save your results by choosing save > attack results but I believe this functionality is limited to users of the professional version found Here . I'm sure you can figure something out in the interim!