Quick post, I just wanted to give some instructions on using BurpSuite when attempting to proxy traffic coming from the Android Emulator.
In order to do this you will want to use Ubuntu. I've got it working on both Ubuntu 9.04 & 9.10. Don't even try with Windows..........its not worth the headache.
1) Download the Android SDK Here.
2) Extract it somewhere (I chose /home/dojo). Yes I'm giving the example on the web security dojo VM :-)
3) Navigate to the extracted folder. For instance, /home/dojo/android-sdk-linux_86/tools/
4) Once in the tools directory (DO NOT INSTALL AS ROOT) type ./android to start up the SDK install.
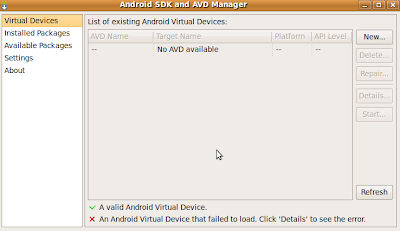
5) At this point you should see the following screen:
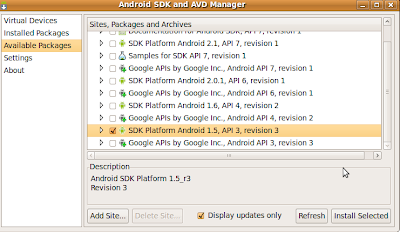
6) Navigate to 'Available Packages' on the left pane, click on the check box and select the following four packages as shown in the figure below.
7) Choose to 'Accept All' and then click install.
8) Now close the dialog box and close the ./android application.
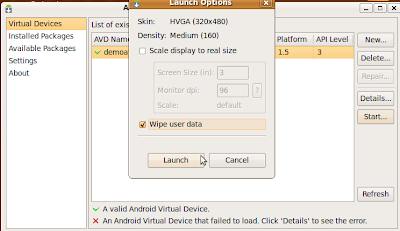
9) Now restart the ./android application and navigate to 'Virtual Devices' on the left pane.
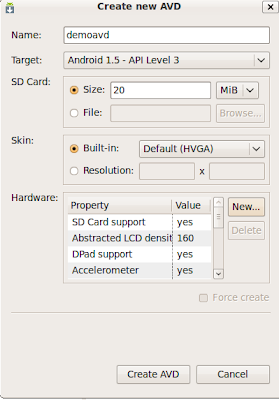
10) Select 'new', give it a name, select 'Target' and choose 'Android 2.1- API Level 7'. Click 'Create AVD'.
11) Start up Burp (this is assuming you have Java installed btw, make sure you do, just "google" installing java on Ubuntu). Change Burp proxy from "Listen on loopback interface only" TO "Support invisible proxying for non-aware clients".
12) Close out the ./android application. In the same directory launch ./emulator. Do so using the following switches as an example
./emulator -avd my_avd -http-proxy http://127.0.0.1:8001 (My Burp instance is running on port 8001)
13) If everything went smoothly, Android booted up and all web traffic is proxied via Burp. You can test by opening the browser.
Note: If you'd like to see the responses coming back to the application ensure you modify your proxy options to intercept server responses if and add the line I've highlighted in the figure below.
In order to do this you will want to use Ubuntu. I've got it working on both Ubuntu 9.04 & 9.10. Don't even try with Windows..........its not worth the headache.
1) Download the Android SDK Here.
2) Extract it somewhere (I chose /home/dojo). Yes I'm giving the example on the web security dojo VM :-)
3) Navigate to the extracted folder. For instance, /home/dojo/android-sdk-linux_86/tools/
4) Once in the tools directory (DO NOT INSTALL AS ROOT) type ./android to start up the SDK install.
5) At this point you should see the following screen:
6) Navigate to 'Available Packages' on the left pane, click on the check box and select the following four packages as shown in the figure below.
7) Choose to 'Accept All' and then click install.
8) Now close the dialog box and close the ./android application.
9) Now restart the ./android application and navigate to 'Virtual Devices' on the left pane.
10) Select 'new', give it a name, select 'Target' and choose 'Android 2.1- API Level 7'. Click 'Create AVD'.
11) Start up Burp (this is assuming you have Java installed btw, make sure you do, just "google" installing java on Ubuntu). Change Burp proxy from "Listen on loopback interface only" TO "Support invisible proxying for non-aware clients".
12) Close out the ./android application. In the same directory launch ./emulator. Do so using the following switches as an example
./emulator -avd my_avd -http-proxy http://127.0.0.1:8001 (My Burp instance is running on port 8001)
13) If everything went smoothly, Android booted up and all web traffic is proxied via Burp. You can test by opening the browser.
Note: If you'd like to see the responses coming back to the application ensure you modify your proxy options to intercept server responses if and add the line I've highlighted in the figure below.